Abstract:
Intelligence collection methods play a pivotal role in supporting national security, strategic decision-making, and planning. This PhD essay provides a comprehensive exploration of these essential techniques, delving into their intricacies, strengths, weaknesses, and ethical implications. Through an in-depth analysis of human intelligence (HUMINT), signals intelligence (SIGINT), geospatial intelligence (GEOINT), measurement and signature intelligence (MASINT), open source intelligence (OSINT), cyber intelligence (CYBINT), imagery intelligence (IMINT), covert intelligence collection, technical intelligence (TECHINT), and the measurement of effectiveness in intelligence gathering, this paper offers a holistic understanding of contemporary intelligence practices.
Additionally, the essay explores emerging trends in intelligence collection, such as technological advancements and the integration of artificial intelligence (AI), while emphasizing the importance of ethics and governance in the context of national security. The knowledge gained from this research enables decision-makers and intelligence agencies to make informed choices, striking a balance between safeguarding nations and upholding fundamental ethical principles.
Introduction
Intelligence collection methods play an integral role in ensuring national security in our increasingly complex and interconnected world. The collection of accurate and timely intelligence has become a cornerstone of modern defense and strategic planning, enabling governments and organizations to make informed decisions, assess risks, and respond effectively to evolving threats.-
Objective: Extensive exploration of various intelligence collection techniques, including:
- Human Intelligence (HUMINT)
- Signals Intelligence (SIGINT)
- Geospatial Intelligence (GEOINT)
- Measurement and Signature Intelligence (MASINT)
- Open Source Intelligence (OSINT)
- Cyber Intelligence (CYBINT)
- Imagery Intelligence (IMINT)
- Covert Intelligence Collection
- Technical Intelligence (TECHINT)
-
Analysis:
- Strengths, weaknesses, and ethical considerations of each method
- Importance of robust intelligence gathering for national security and decision-making
-
Implications:
- Proactive threat countermeasures with accurate intelligence
- Risks of inadequate or inaccurate intelligence
-
Research emphasis:
- Critical role of intelligence collection techniques in national security and strategic decision-making
-
Exploration of emerging trends:
- Integration of AI and big data analytics in intelligence practices
-
Ethical considerations:
- Transparency, accountability, and protection of individual rights and privacy
-
Aim:
- Contribution to a safer and more secure world through an improved understanding of intelligence collection methods.
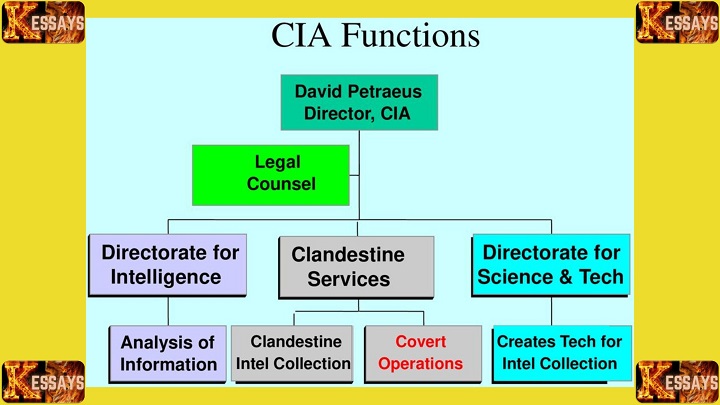
Human Intelligence (HUMINT)
2.1 Definition and Scope of HUMINT:
- HUMINT is an intelligence collection method that involves gathering information through direct human interactions and sources.
- It encompasses acquiring data from individuals, informants, assets, and agents who have access to valuable intelligence.
- HUMINT provides unique insights into intentions, motivations, and human networks that may not be accessible through other means.
2.2 Sources of HUMINT:
- Agents: Trained individuals who work undercover to collect intelligence from within target organizations or regions.
- Informants: Individuals who voluntarily provide information to intelligence agencies, often motivated by various factors, such as monetary rewards or ideological beliefs.
- Defectors: Individuals who leave their organizations or countries and provide valuable intelligence due to disillusionment, fear, or personal motives.
- Interrogations: Extracting information through interviews and interrogations of individuals with relevant knowledge.
2.3 Operational Challenges and Limitations of HUMINT:
- Human Reliability: The reliability and credibility of human sources can be difficult to ascertain, leading to potential inaccuracies or deception.
- Security Risks: Operating undercover in hostile environments poses significant risks to the safety of agents and informants.
- Limited Coverage: HUMINT operations are resource-intensive and may not provide comprehensive coverage in large-scale intelligence gathering.
- Language and Cultural Barriers: Interacting with sources from different cultural backgrounds may hinder effective communication and understanding.
2.4 Ethical Considerations in HUMINT:
- Informed Consent: Respecting the rights and autonomy of sources by obtaining their informed consent before gathering information.
- Protection of Sources: Safeguarding the identity and safety of sources to prevent reprisals and ensure their ongoing cooperation.
- Human Rights: Balancing the need for intelligence with the principles of human rights, ensuring that sources are not subjected to unethical treatment.
- Covert Operations: Ethical concerns arise when HUMINT operations involve manipulation, entrapment, or coercion.
Signals Intelligence (SIGINT)
3.1 Overview of SIGINT:
- SIGINT is an intelligence collection method that involves intercepting and analyzing signals, communications, and electronic emissions.
- It plays a crucial role in gathering intelligence from various sources, including radio, satellite, cellular, and internet communications.
- SIGINT provides insights into the activities, intentions, and capabilities of foreign entities and adversaries.
3.2 Types of SIGINT Collection:
- Communications Intelligence (COMINT): Involves intercepting and analyzing voice and data communications, such as phone calls, emails, and messaging.
- Electronic Intelligence (ELINT): Focuses on non-communications signals, such as radar emissions and electronic signatures from weapons systems and electronic devices.
- Foreign Instrumentation Signals Intelligence (FISINT): Targets signals emitted by foreign weapon systems, telemetry, and other technical intelligence data.
3.3 Technical Aspects and Advancements in SIGINT:
- Signal Interception: Advanced antennas, receivers, and satellites are used to intercept a wide range of signals across various frequencies and platforms.
- Signal Processing: Powerful computing systems analyze intercepted signals, extracting valuable intelligence through decryption and pattern recognition.
- Cyber SIGINT: The emergence of cyberspace has expanded SIGINT capabilities, allowing for the collection of electronic intelligence from digital networks and systems.
3.4 Legal and Privacy Issues in SIGINT:
- Privacy Concerns: The extensive collection and analysis of electronic communications raise concerns about the privacy and civil liberties of individuals.
- Fourth Amendment: In democratic societies, SIGINT activities are often subject to legal restrictions, ensuring compliance with constitutional protections against unreasonable searches and seizures.
- Oversight and Accountability: SIGINT agencies are subject to oversight by legislative bodies and independent agencies to prevent abuses of power and protect citizens' rights.
- International Law: Cross-border SIGINT operations may raise legal and diplomatic challenges related to sovereignty and espionage.
Geospatial Intelligence (GEOINT)
4.1 Understanding GEOINT and Its Applications:
- GEOINT is an intelligence discipline that utilizes geospatial data to provide a comprehensive understanding of the Earth's surface and its features.
- It involves the collection, analysis, and visualization of data from various sources, such as satellites, drones, aerial imagery, and geographic information systems (GIS).
- GEOINT applications span a wide range of sectors, including defense, disaster response, environmental monitoring, urban planning, and agriculture.
4.2 Satellite Imagery and Remote Sensing:
- Satellite imagery forms a significant part of GEOINT, offering high-resolution images of Earth's surface from space.
- Remote sensing technologies, including multispectral and hyperspectral imaging, capture valuable data beyond visible light, such as infrared and microwave signals.
- These images and data facilitate the monitoring of changes in land use, environmental conditions, and natural resources.
4.3 Geospatial Data Analysis and Interpretation:
- Geospatial analysts process and interpret vast amounts of data collected through various sources.
- Advanced algorithms and artificial intelligence aid in detecting patterns, anomalies, and correlations, providing valuable intelligence insights.
- Geospatial data analysis supports decision-making in disaster response, resource management, and identifying potential threats in military operations.
4.4 GEOINT in Civilian and Military Contexts:
- In the civilian context, GEOINT aids in urban planning, infrastructure development, and environmental conservation.
- Disaster response agencies use GEOINT to assess damage and coordinate relief efforts during natural disasters.
- In the military realm, GEOINT enhances situational awareness, mission planning, and target identification.
- GEOINT enables defense agencies to track adversaries, assess potential threats, and monitor critical infrastructure.
Measurement and Signature Intelligence (MASINT)
5.1 The Nature of MASINT:
- MASINT is an intelligence discipline that focuses on measuring and analyzing unique physical attributes and signatures of targets.
- It complements other intelligence disciplines by providing specialized information that cannot be obtained through traditional means.
- MASINT data includes a wide range of measurements, such as nuclear radiation, electromagnetic emissions, and seismic vibrations.
5.2 MASINT Sensors and Techniques:
- MASINT employs various sensors and techniques to collect data, including:
- Radar and LIDAR: Using radio waves and lasers to measure distances and identify objects.
- Spectroscopy: Analyzing the unique electromagnetic signatures of materials for identification.
- Acoustic Sensors: Detecting sounds and vibrations to infer activities or events.
- Nuclear Radiation Detectors: Monitoring radiation levels for nuclear-related intelligence.
- Electro-Optical and Infrared (EO/IR) Sensors: Capturing visual and heat signatures from targets.
5.3 Challenges and Potential of MASINT:
- Complexity: MASINT data can be intricate and require specialized analysis and interpretation.
- Integration: Combining data from different MASINT sensors can be challenging but leads to a more comprehensive intelligence picture.
- Sensitivity: Environmental factors may impact MASINT sensor accuracy and effectiveness.
- Target Elusiveness: Some targets may actively evade MASINT detection, posing challenges to data collection.
5.4 Ensuring Accuracy and Reliability in MASINT:
- Calibration: Regular calibration of MASINT sensors is essential for accurate measurements.
- Validation: Corroborating MASINT data with information from other intelligence sources enhances its reliability.
- Expertise: Well-trained analysts with expertise in MASINT technologies are critical for accurate interpretation.
- Quality Control: Implementing rigorous quality control measures during data collection and analysis ensures the credibility of MASINT intelligence.
Open Source Intelligence (OSINT)
6.1 Defining OSINT and Its Relevance:
- OSINT is an intelligence collection method that involves gathering information from publicly available sources.
- It includes data from newspapers, websites, social media, public records, academic papers, and other publicly accessible information.
- OSINT is increasingly relevant in the digital age due to the vast amount of data available and its potential to provide valuable insights for various purposes, including national security, business intelligence, and investigative journalism.
6.2 OSINT Collection from Publicly Available Sources:
- OSINT analysts collect information from a wide range of sources, such as:
- News websites and articles
- Government and organizational websites
- Academic publications and research papers
- Blogs and forums
- Public records and government databases
6.3 Leveraging Social Media for Intelligence Gathering:
- Social media platforms have become a significant source of OSINT due to the abundance of user-generated content.
- OSINT analysts monitor social media channels for real-time information, opinions, sentiments, and geolocation data.
- Social media posts and interactions may provide insights into current events, public sentiment, and potential threats.
6.4 Evaluating and Verifying OSINT Data:
- OSINT analysts must critically evaluate the reliability and credibility of the collected data.
- Verifying the authenticity of information is crucial to avoid spreading misinformation or using inaccurate data for decision-making.
- Cross-referencing OSINT data with information from multiple sources helps ensure accuracy and validity.
Cyber Intelligence (CYBINT)
7.1 The Emergence of CYBINT in the Digital Age:
- CYBINT is a specialized intelligence discipline that focuses on gathering and analyzing data related to cyber threats and vulnerabilities.
- With the rapid growth of the digital age, the increasing reliance on technology, and the prevalence of cyberattacks, CYBINT has emerged as a critical component of modern intelligence gathering.
- It aims to provide insights into cyber threats, attackers' tactics, techniques, and procedures (TTPs), and potential vulnerabilities in digital systems.
7.2 Cyber Threat Intelligence (CTI) and Its Significance:
- CTI involves the collection and analysis of data to understand and anticipate cyber threats.
- It provides timely and actionable information to organizations, enabling them to proactively defend against cyberattacks.
- CTI helps organizations enhance their cybersecurity posture, incident response capabilities, and risk management strategies.
7.3 Techniques for Cyber Intelligence Collection:
- Passive Collection: Monitoring open-source data, dark web forums, and public information for cyber threat indicators.
- Active Collection: Engaging in ethical hacking, honeypots, and decoy networks to lure and analyze potential attackers.
- Collaboration: Sharing threat intelligence with other organizations and cybersecurity communities to create a collective defense against cyber threats.
- Technical Analysis: Conducting in-depth analysis of malware, network traffic, and intrusion attempts to identify attack patterns.
7.4 Legal and Ethical Challenges in CYBINT:
- Privacy Concerns: Collecting cyber intelligence may involve monitoring individuals' online activities, raising privacy and civil liberties issues.
- Jurisdictional Challenges: Cyber threats often cross national borders, requiring cooperation and adherence to international law in intelligence gathering.
- Offensive Operations: Engaging in offensive CYBINT activities, such as hacking back, may raise legal and ethical questions about potential retaliation and escalation.
- Attribution: Accurately attributing cyberattacks to specific actors can be challenging and may have legal and diplomatic implications.
Imagery Intelligence (IMINT)
8.1 Introduction to IMINT and its Evolution:
- IMINT is an intelligence discipline that involves collecting, analyzing, and interpreting visual imagery from various sources.
- It has a rich history, dating back to the use of aerial reconnaissance in the early 20th century, and has evolved significantly with advancements in technology.
- IMINT plays a crucial role in providing valuable insights into the activities, facilities, and terrain of interest.
8.2 IMINT Sensors and Platforms:
- IMINT employs a variety of sensors and platforms to capture visual imagery:
- Satellites: High-resolution satellites provide comprehensive global coverage, offering images from space.
- Drones (Unmanned Aerial Vehicles - UAVs): UAVs offer real-time and on-demand aerial imagery for targeted areas.
- Aircraft: Manned aircraft equipped with imaging sensors can provide flexibility and detailed coverage.
- Ground-based Sensors: Fixed or mobile ground-based sensors capture imagery for specific locations or scenarios.
8.3 Interpretation and Analysis of IMINT Data:
- IMINT data analysts interpret and analyze the visual imagery to extract valuable intelligence.
- Photogrammetry techniques are used to measure distances, elevations, and object dimensions from imagery.
- Imagery analysts identify and interpret objects, facilities, infrastructure, and changes over time, contributing to situational awareness and intelligence reporting.
8.4 Advancements in IMINT Technologies:
- High-Resolution Imagery: Advancements in satellite and sensor technologies offer increasingly detailed and sharp imagery.
- Hyperspectral Imaging: Hyperspectral sensors capture data across multiple spectral bands, enabling advanced material and vegetation analysis.
- Synthetic Aperture Radar (SAR): SAR sensors penetrate clouds and provide all-weather imaging, crucial for military and disaster response applications.
- 3D Reconstruction: IMINT technologies now enable the creation of three-dimensional models from imagery, enhancing visualization and analysis capabilities.
Covert Intelligence Collection
9.1 Covert Operations and Intelligence Gathering:
- Covert intelligence collection involves conducting secret operations to gather information without the target's knowledge.
- Covert agents may operate undercover or use clandestine techniques to obtain sensitive or classified information.
- Covert operations aim to protect the identity of intelligence personnel and the sources involved to maintain the element of surprise and avoid detection.
9.2 Importance of Covert Collection in National Security:
- Covert intelligence collection is essential for obtaining information from high-risk or hostile environments where overt methods are not feasible.
- It allows intelligence agencies to gather critical data on adversaries, terrorist organizations, and other threats without tipping them off.
- Covert collection enhances strategic advantage by enabling preemptive actions and countering potential threats before they materialize.
9.3 Ethical and Legal Implications of Covert Intelligence Collection:
- Ethical Considerations: Covert operations may involve deception, manipulation, and other covert tactics that can raise ethical dilemmas.
- Proportionality: The benefits of covert intelligence collection should outweigh potential risks and the impact on individuals' rights.
- Accountability: Covert operations require stringent oversight to ensure transparency, adherence to legal boundaries, and respect for human rights.
- Rule of Law: Covert collection must align with domestic and international laws, avoiding extrajudicial actions and violating sovereignty.
Technical Intelligence (TECHINT)
10.1 Understanding TECHINT and its Objectives:
- TECHINT is an intelligence discipline that focuses on the collection and analysis of technical data related to foreign weapon systems, equipment, and technologies.
- Its primary objective is to gain insights into the capabilities, vulnerabilities, and advancements of adversaries' military hardware and technological infrastructure.
- TECHINT plays a critical role in supporting defense planning, acquisition decisions, and countering potential threats posed by foreign technologies.
10.2 Collection Techniques in TECHINT:
- Analysis of Captured Equipment: Studying and reverse-engineering captured enemy equipment or weapons to understand their design and capabilities.
- Signal Intelligence (SIGINT): Intercepting and analyzing electronic emissions and communications related to foreign weapon systems and technology.
- Imagery Intelligence (IMINT): Utilizing satellite and aerial imagery to monitor and assess foreign military installations, equipment, and facilities.
- Cyber Intelligence (CYBINT): Collecting technical data related to cyber threats and cyber capabilities of foreign actors.
10.3 Challenges and Limitations in TECHINT:
- Access to Technology: Gaining access to advanced foreign technologies and weapon systems can be challenging and sometimes restricted.
- Technological Complexity: Understanding and analyzing sophisticated technologies often require specialized expertise and infrastructure.
- Deception and Disinformation: Adversaries may employ deception techniques to mislead TECHINT efforts and protect their true capabilities.
- Rapid Advancements: The fast pace of technological advancements poses challenges in staying up-to-date with the latest developments.
10.4 Integration of TECHINT with Other Intelligence Disciplines:
- Combining TECHINT with other intelligence disciplines, such as HUMINT, SIGINT, and IMINT, provides a comprehensive intelligence picture.
- HUMINT can provide insights into the intentions and decision-making processes behind the development of foreign technologies.
- SIGINT complements TECHINT by providing electronic intelligence on the communication and electronic signatures of foreign technologies.
- IMINT contributes to TECHINT by providing visual imagery and situational context to support the analysis of foreign military equipment.
Measurement of Effectiveness in Intelligence Collection
11.1 Metrics for Assessing Intelligence Collection Success:
- Timeliness: The ability to provide intelligence in a timely manner, allowing decision-makers to respond quickly to emerging threats.
- Accuracy: The degree to which collected intelligence aligns with ground truth and reality, ensuring reliable and trustworthy information.
- Relevance: Intelligence should be pertinent to the mission or objectives, addressing specific needs and supporting decision-making.
- Completeness: Ensuring that intelligence provides a comprehensive view of the situation or target, leaving no critical gaps in understanding.
- Actionability: Intelligence should be actionable, providing clear recommendations or insights for follow-up actions.
11.2 Challenges in Measuring Intelligence Collection Effectiveness:
- Attribution: Identifying the direct impact of intelligence collection on specific outcomes can be challenging due to the complexity of geopolitical situations.
- Covert Operations: Covert intelligence activities make it difficult to assess their effectiveness openly, as their success relies on maintaining secrecy.
- Information Overload: The volume of collected data can be overwhelming, making it challenging to filter and analyze relevant intelligence effectively.
- Long-Term Impact: Some intelligence actions may yield results over an extended period, making it challenging to attribute success to specific efforts.
11.3 Improving Intelligence Collection through Feedback and Iteration:
- Continuous Assessment: Regularly reviewing the effectiveness of intelligence collection methods and adjusting strategies accordingly.
- Analyst Feedback: Involving intelligence analysts in the evaluation process, as they can provide insights into the strengths and weaknesses of data collection techniques.
- Interagency Collaboration: Promoting collaboration among different intelligence agencies and disciplines to leverage each other's strengths and improve overall effectiveness.
- Technological Advancements: Embracing new technologies and tools to enhance data collection, analysis, and visualization capabilities.
- Red Teaming: Engaging in red teaming exercises to simulate potential threats and assess intelligence collection responses.
Read Also: Police Community Relations: Building Trust and Collaboration
Future Trends in Intelligence Collection
12.1 Technological Advancements and their Impact on Intelligence Gathering:
- Advanced Sensors: Continued advancements in sensors, such as hyperspectral imaging and quantum sensors, will enhance data collection capabilities, providing more detailed and accurate intelligence.
- Space-based Intelligence: Smaller, more cost-effective satellites and constellations will enable continuous global coverage and real-time monitoring.
- Big Data Analytics: Advanced data analytics and machine learning algorithms will help process vast amounts of data from diverse sources, extracting valuable intelligence insights.
- Internet of Things (IoT): The proliferation of interconnected devices will create new opportunities for intelligence collection and monitoring, along with cybersecurity challenges.
- Blockchain: Adoption of blockchain technology may impact intelligence gathering by increasing data security and transparency in transactions and communications.
12.2 The Role of Artificial Intelligence in Intelligence Collection:
- Automated Data Collection: AI-powered bots and web crawlers can automatically collect information from online sources, streamlining open-source intelligence (OSINT) gathering.
- Predictive Analysis: AI algorithms can identify patterns and trends in data, facilitating predictive analysis for anticipating threats and potential developments.
- Natural Language Processing (NLP): NLP enables better analysis of unstructured data, such as text from social media or news articles, aiding in sentiment analysis and understanding public opinion.
- Image and Speech Recognition: AI-powered image and speech recognition technologies will enhance analysis of multimedia data, supporting IMINT and voice-based intelligence gathering.
12.3 Ethics and Governance in the Era of Advanced Intelligence Methods:
- Privacy and Surveillance: As intelligence collection becomes more sophisticated, concerns about privacy, data protection, and surveillance will intensify.
- Bias and Fairness: AI algorithms may inherit biases from training data, raising ethical concerns about fair and unbiased intelligence analysis.
- Accountability and Oversight: Advanced intelligence methods require robust governance frameworks to ensure transparency, accountability, and adherence to legal and ethical standards.
- Dual-Use Technologies: The same advanced technologies used for intelligence gathering may also be misused for malicious purposes, calling for responsible usage and export control measures.

Comments are closed!