Intelligence Collection Methods
Human Intelligence (HUMINT)
Human Intelligence remains one of the most traditional and widely used methods of information gathering. It involves direct interaction with people, through espionage, debriefings, interviews, or cultivation of informants, to obtain insights that technology alone cannot reveal. HUMINT provides valuable context, nuance, and cultural understanding, though it is vulnerable to misinformation, deception, and the reliability of human sources.
Signals Intelligence (SIGINT)
Signals Intelligence focuses on the interception and analysis of communications and electronic signals. By monitoring telephone conversations, radio transmissions, and digital communications, SIGINT provides critical insights into adversaries’ intentions, capabilities, and operations. Its effectiveness lies in its ability to collect large amounts of data, but this same advantage can also overwhelm analysts and raise ethical concerns about surveillance and privacy.
Geospatial Intelligence (GEOINT)
Geospatial Intelligence uses imagery and spatial data from satellites, drones, and other aerial platforms to create maps, track movements, and monitor activities across vast areas. GEOINT is essential in both military and humanitarian operations, offering real-time assessments of terrain, infrastructure, and environmental changes. However, it requires sophisticated technology and often depends on weather conditions and visibility for accuracy.
Measurement and Signature Intelligence (MASINT)
Measurement and Signature Intelligence involves detecting, tracking, and analyzing distinctive physical and scientific signatures, such as radar emissions, nuclear radiation, or chemical traces. MASINT plays a crucial role in identifying activities that cannot be seen or heard through conventional means, making it particularly valuable for monitoring weapons development and testing. Its complexity, however, demands advanced expertise and expensive equipment.
Open Source Intelligence (OSINT)
Open Source Intelligence refers to information collected from publicly available sources, including news outlets, academic research, social media platforms, and government reports. OSINT is cost-effective and often provides immediate insights into global developments. Yet, its reliability can be compromised by misinformation, propaganda, and the overwhelming volume of unverified data circulating in open domains.
Cyber Intelligence (CYBINT)
Cyber Intelligence has become increasingly vital in an era dominated by digital networks. It involves monitoring, analyzing, and defending against threats in cyberspace, including hacking attempts, malware, and online espionage. CYBINT provides early warning against cyberattacks and protects critical infrastructure, but it faces challenges from rapidly evolving digital threats and the anonymity afforded to cyber adversaries.
Imagery Intelligence (IMINT)
Imagery Intelligence relies on visual information captured through satellites, reconnaissance aircraft, and drones. IMINT supports everything from strategic military planning to disaster response by providing clear visual evidence of activities and terrain. Its strength lies in the clarity of its data, but imagery can be limited by environmental conditions, concealment efforts, or lack of context without corroborating intelligence.
Covert Intelligence Collection
Covert collection emphasizes secrecy and deception in gathering sensitive information. It often combines several intelligence methods under clandestine operations, employing undercover agents, surveillance, or cyber intrusions. Covert intelligence is indispensable for high-risk missions but poses significant ethical dilemmas and risks of political fallout if operations are exposed.
Technical Intelligence (TECHINT)
Technical Intelligence is the study and analysis of foreign technologies, equipment, and weapon systems. By examining captured devices, military hardware, or digital systems, analysts can understand an adversary’s technical capabilities and prepare countermeasures. While invaluable for defense planning, TECHINT requires access to advanced materials and technical expertise, making it resource-intensive and sometimes difficult to obtain.
Analysis and Implications
Each of these methods brings unique strengths but also distinct limitations. HUMINT provides deep contextual understanding but is vulnerable to deception and requires extensive resources to maintain networks of informants. SIGINT and GEOINT are invaluable in scope but can overwhelm analysts with vast amounts of raw data, raising concerns about accuracy and interpretation. MASINT and TECHINT often demand advanced technology and specialized expertise, making them costly to deploy. OSINT and CYBINT are increasingly powerful in the digital age, but they raise questions about misinformation, data manipulation, and privacy.
A central challenge lies in balancing effectiveness with ethics. The same tools that protect national security can, if misused, undermine civil liberties and erode public trust. The growing integration of artificial intelligence and big data analytics offers unprecedented opportunities to process vast amounts of information quickly and identify patterns invisible to human analysts. However, these advancements also heighten the risks of surveillance overreach, algorithmic bias, and the erosion of accountability.
The stakes of intelligence collection are high. When accurate and reliable, intelligence enables proactive measures that prevent crises before they escalate. When flawed, inadequate, or misinterpreted, it can lead to failed strategies, unnecessary conflicts, and even humanitarian disasters.
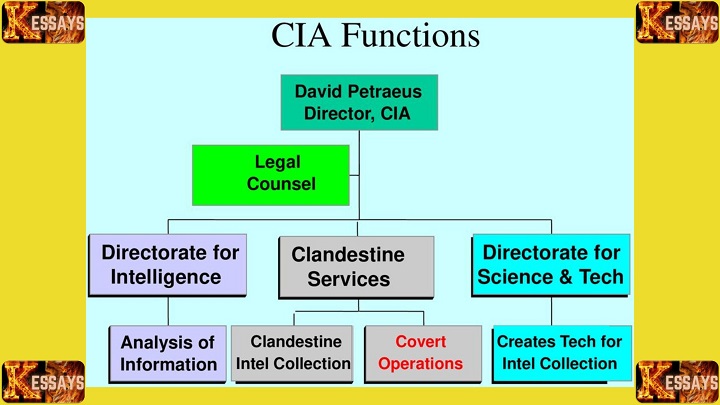
Human Intelligence (HUMINT)
2.1 Definition and Scope of HUMINT
Human Intelligence (HUMINT) is an intelligence collection method that relies on direct human interactions and sources. It involves acquiring information from individuals, informants, assets, and agents who have access to valuable insights. Unlike technical forms of intelligence, HUMINT captures the intentions, motivations, and interpersonal dynamics that often remain hidden from other collection techniques.
2.2 Sources of HUMINT
-
Agents: Trained operatives who work undercover within target organizations or regions to gather intelligence.
-
Informants: Individuals who voluntarily provide information, often motivated by financial gain, ideology, or personal grievances.
-
Defectors: People who abandon their organizations or countries and share sensitive intelligence, typically driven by disillusionment, fear, or personal motives.
-
Interrogations: Structured interviews or questioning of individuals with relevant knowledge, used to extract critical information.
2.3 Operational Challenges and Limitations of HUMINT
HUMINT faces significant challenges that impact its reliability and effectiveness. Human sources are not always dependable, as deception, misinformation, or shifting loyalties can compromise accuracy. Undercover operations in hostile environments expose agents and informants to severe personal risk. Additionally, HUMINT is resource-intensive and provides limited coverage compared to technical intelligence methods, making it difficult to apply on a large scale. Language differences, cultural barriers, and misinterpretation further complicate interactions with sources from diverse backgrounds.
2.4 Ethical Considerations in HUMINT
HUMINT raises profound ethical questions. Respecting the autonomy of sources by ensuring informed consent is essential, though not always feasible in covert operations. Agencies must prioritize the protection of sources, safeguarding their identity and security to prevent reprisals. Equally important is adherence to human rights standards, ensuring individuals are not subjected to coercion, mistreatment, or entrapment during intelligence collection. The inherent secrecy of HUMINT operations heightens the need for accountability and ethical oversight.
In conclusion, HUMINT remains a critical intelligence collection method, providing valuable insights into human factors that shape decision-making and actions. However, the operational challenges and ethical considerations associated with HUMINT necessitate a balanced approach that respects the rights of sources while fulfilling the objectives of national security and strategic intelligence gathering.Read Also: National Intelligence Model: A Comprehensive Overview
Signals Intelligence (SIGINT)
3.1 Overview of SIGINT
Signals Intelligence (SIGINT) is the collection and analysis of signals, communications, and electronic emissions. It is one of the most technologically driven intelligence methods, enabling the interception of data from radio, satellite, cellular, and internet-based systems. By monitoring these signals, SIGINT provides insights into the activities, intentions, and capabilities of foreign governments, organizations, and adversaries, making it indispensable for both military and national security operations.
3.2 Types of SIGINT Collection
-
Communications Intelligence (COMINT): Involves intercepting and analyzing voice and data communications such as phone calls, emails, and digital messages. COMINT helps reveal adversary intentions, plans, and internal discussions.
-
Electronic Intelligence (ELINT): Focuses on the collection of non-communication signals, such as radar emissions, navigation systems, and other electronic signatures from weapons and defense systems. ELINT is especially valuable for monitoring military capabilities.
-
Foreign Instrumentation Signals Intelligence (FISINT): Targets signals associated with the testing and operation of foreign weapon systems, such as telemetry data and missile guidance signals. FISINT provides technical insights into weapons development and performance.
3.3 Technical Aspects and Advancements in SIGINT
Modern SIGINT relies on sophisticated tools and technologies to capture and interpret signals. Advanced antennas, receivers, and satellites are employed to intercept signals across a wide frequency spectrum. Once intercepted, signals undergo complex processing, including decryption, translation, and pattern recognition, to extract actionable intelligence. With the rise of cyberspace, SIGINT has expanded into digital domains, often referred to as Cyber SIGINT, which involves monitoring internet traffic, data packets, and online communication networks. These advancements have significantly enhanced the speed, scope, and accuracy of intelligence gathering.
3.4 Legal and Privacy Issues in SIGINT
Despite its effectiveness, SIGINT raises important legal and ethical challenges. The large-scale collection of communications data can infringe on individual privacy and civil liberties. In democratic societies, constitutional protections, such as the Fourth Amendment in the United States, restrict surveillance practices to prevent unlawful searches and seizures. Oversight mechanisms, including legislative committees and independent review boards, play a crucial role in ensuring accountability and preventing abuse of SIGINT powers. On the international stage, cross-border SIGINT operations often raise diplomatic concerns, as they may be perceived as violations of sovereignty and international law.
In conclusion, SIGINT remains a powerful intelligence collection method, providing vital information about adversaries and potential threats. Its various types of collection, technical advancements, and cyber capabilities enhance its effectiveness in the digital age. However, legal and privacy considerations demand a delicate balance between intelligence needs and individual rights, ensuring responsible and accountable use of SIGINT capabilities in safeguarding national security.
Geospatial Intelligence (GEOINT)
4.1 Understanding GEOINT and Its Applications
Geospatial Intelligence (GEOINT) is an intelligence discipline that integrates geospatial data to provide a detailed understanding of the Earth’s surface, its features, and human activity within it. It combines the collection, analysis, and visualization of information from sources such as satellites, drones, aerial reconnaissance, and geographic information systems (GIS). The versatility of GEOINT makes it valuable across multiple sectors, including defense, disaster response, environmental monitoring, urban planning, and agriculture.
4.2 Satellite Imagery and Remote Sensing
A central component of GEOINT is satellite imagery, which delivers high-resolution views of the Earth from orbit. Remote sensing technologies enhance this capability by capturing data beyond the visible spectrum, including infrared, radar, and microwave signals. Multispectral and hyperspectral imaging, for example, allow analysts to detect subtle changes in vegetation, water quality, or soil composition. Together, these tools enable the monitoring of environmental shifts, resource distribution, and land use changes on a global scale.
4.3 Geospatial Data Analysis and Interpretation
The vast amount of data produced through geospatial collection requires sophisticated analysis to extract meaningful insights. Geospatial analysts employ advanced algorithms, machine learning, and artificial intelligence to identify patterns, detect anomalies, and establish correlations across datasets. These analytical capabilities support decision-making in diverse fields: guiding military operations, improving disaster preparedness and response, and informing sustainable resource management. By transforming raw imagery and sensor data into actionable intelligence, GEOINT strengthens both strategic planning and operational execution.
4.4 GEOINT in Civilian and Military Contexts
The applications of GEOINT extend far beyond the defense sector. In civilian contexts, it supports urban planning, infrastructure development, and environmental conservation. Humanitarian organizations and disaster response agencies rely on GEOINT to assess damage, track population displacement, and coordinate relief operations during natural disasters. In the military domain, GEOINT provides enhanced situational awareness, supports mission planning, and assists in precision targeting. It enables defense agencies to track adversary movements, monitor critical infrastructure, and anticipate potential threats with greater accuracy.
In conclusion, Geospatial Intelligence (GEOINT) offers a comprehensive understanding of Earth's surface and its dynamic features through the collection and analysis of geospatial data. Utilizing satellite imagery, remote sensing technologies, and advanced data analysis techniques, GEOINT finds applications in civilian sectors like urban planning, disaster response, and environmental monitoring. In the military realm, GEOINT significantly enhances situational awareness, mission planning, and target identification, providing valuable intelligence to safeguard nations and support strategic decision-making.Read Also: The Crucial Role of Counterintelligence
Measurement and Signature Intelligence (MASINT)
5.1 The Nature of MASINT
Measurement and Signature Intelligence (MASINT) is a specialized intelligence discipline that focuses on detecting, measuring, and analyzing the distinctive physical signatures of targets. It supplements other intelligence methods by providing highly technical information that cannot be obtained through traditional collection techniques. MASINT data encompasses a wide range of measurable phenomena, including nuclear radiation, electromagnetic emissions, acoustic signatures, seismic activity, and thermal patterns. This unique focus makes it indispensable for monitoring weapons systems, detecting concealed activities, and verifying treaty compliance.
5.2 MASINT Sensors and Techniques
MASINT relies on an array of advanced sensors and collection methods. Radar and Light Detection and Ranging (LIDAR) systems measure distances and map objects with precision, while spectroscopy identifies the electromagnetic “fingerprints” of specific materials. Acoustic sensors capture vibrations and sound waves, providing clues about movement, construction, or weapons testing. Nuclear radiation detectors monitor potential nuclear activities, while electro-optical and infrared (EO/IR) sensors capture visual and thermal signatures. Together, these technologies generate detailed profiles of targets and environments that enhance overall intelligence assessments.
5.3 Challenges and Potential of MASINT
The value of MASINT lies in its technical depth, but this also presents significant challenges. Its data is often highly complex, requiring specialized expertise and advanced computational tools to interpret accurately. Integrating multiple streams of MASINT data with other intelligence disciplines can be difficult, yet when achieved, it produces a more complete and reliable intelligence picture. Environmental conditions, such as weather, terrain, or background noise, may interfere with sensor accuracy. Furthermore, sophisticated adversaries may deliberately attempt to mask or alter their signatures, complicating collection efforts. Despite these challenges, MASINT has vast potential, particularly in identifying hidden threats and verifying the authenticity of other intelligence.
5.4 Ensuring Accuracy and Reliability in MASINT
The credibility of MASINT depends on rigorous standards of accuracy and reliability. Regular calibration of sensors ensures precision in measurement, while cross-validation with data from other intelligence sources enhances confidence in findings. Skilled analysts with deep technical expertise are essential for interpreting complex MASINT outputs. Finally, strict quality control procedures during collection and analysis safeguard against errors and strengthen the discipline’s overall contribution to national security.
In conclusion, Measurement and Signature Intelligence (MASINT) play a vital role in intelligence gathering, focusing on unique physical attributes and signatures of targets. Through a variety of sensors and techniques, MASINT provides valuable data that complements other intelligence disciplines. Overcoming challenges in data complexity, integration, sensitivity, and target elusiveness is essential to maximize the potential of MASINT. Ensuring accuracy and reliability through calibration, validation, expertise, and quality control further enhances its value in supporting decision-making and providing critical insights for national security and defense.
Open Source Intelligence (OSINT)
6.1 Defining OSINT and Its Relevance
Open Source Intelligence (OSINT) refers to the systematic collection and analysis of information from publicly accessible sources. These sources include newspapers, websites, social media platforms, government publications, academic journals, and other forms of openly available data. In today’s digital era, OSINT has become increasingly relevant due to the sheer volume of information generated and shared online. It supports multiple fields, ranging from national security and counterterrorism to corporate strategy, business intelligence, and investigative journalism, by offering insights that may otherwise be inaccessible through classified means.
6.2 OSINT Collection from Publicly Available Sources
OSINT analysts employ structured methods to gather information from a wide variety of sources. These include:
-
News websites and articles, which provide updates on global events and political developments.
-
Government and organizational websites, offering official statements, reports, and policy documents.
-
Academic publications and research papers, contributing expert knowledge and peer-reviewed data.
-
Blogs and online forums, where individuals share perspectives, opinions, or insider information.
-
Public records and databases, such as court filings, company registries, and electoral rolls.
The diversity of these sources allows analysts to build a comprehensive intelligence picture that spans multiple domains.
6.3 Leveraging Social Media for Intelligence Gathering
Social media has emerged as one of the most significant contributors to OSINT due to the vast amounts of user-generated content shared in real time. Analysts can monitor platforms such as Twitter, Facebook, and Instagram to gather data on current events, public opinion, sentiment trends, and even geolocation details embedded in posts. For instance, during crises or conflicts, social media often provides the earliest indicators of unfolding events. Beyond crisis monitoring, social media analysis can also help detect emerging threats, identify networks of influence, and understand population dynamics.
6.4 Evaluating and Verifying OSINT Data
Despite its value, OSINT presents challenges related to information overload and credibility. Analysts must critically evaluate the reliability of sources, recognizing that misinformation, bias, and deliberate deception are common in open platforms. Verification is therefore essential, often involving cross-referencing with other OSINT findings or corroborating with classified intelligence such as SIGINT or HUMINT. Establishing source credibility and ensuring contextual accuracy are key to making OSINT both reliable and actionable.
In conclusion, Open Source Intelligence (OSINT) is a valuable intelligence collection method that utilizes publicly available information from a wide range of sources. In the digital age, OSINT plays a significant role in gathering real-time insights and supporting various applications, such as national security and business intelligence. However, careful evaluation and verification of OSINT data are essential to ensure its reliability and effectiveness. By leveraging OSINT effectively, intelligence analysts and decision-makers can gain valuable insights and make informed choices in a rapidly changing and interconnected world.Read Also: Intelligence Gathering Tools: Data Collection Decision-Making
Cyber Intelligence (CYBINT)
7.1 The Emergence of CYBINT in the Digital Age
Cyber Intelligence, or CYBINT, is a specialized field within the broader intelligence discipline that concentrates on the collection and analysis of information related to cyber threats, vulnerabilities, and malicious actors. With the rapid expansion of the digital age and the increasing dependence of governments, businesses, and individuals on interconnected technologies, the risks associated with cyberattacks have escalated significantly. As a result, CYBINT has become a critical component of modern intelligence operations. Its primary aim is to provide insights into emerging cyber threats, understand attackers’ tactics, techniques, and procedures (TTPs), and identify weaknesses within digital infrastructures that could be exploited.
7.2 Cyber Threat Intelligence (CTI) and Its Significance
A key dimension of CYBINT is Cyber Threat Intelligence (CTI), which involves systematically collecting, analyzing, and interpreting data to anticipate and mitigate cyber threats. CTI provides timely, actionable insights that enable organizations to strengthen their defenses and take proactive measures against potential attacks. By integrating CTI into their security frameworks, organizations can not only improve their incident response and recovery efforts but also reinforce their overall risk management strategies. Ultimately, CTI transforms raw cyber data into meaningful intelligence that supports informed decision-making in the face of an evolving cyber threat landscape.
7.3 Techniques for Cyber Intelligence Collection
CYBINT employs a range of collection methods to uncover and analyze threat indicators. Passive collection techniques include monitoring open-source information, dark web forums, and threat reports for early signs of malicious activity. Active collection, on the other hand, involves more direct engagement, such as deploying honeypots or decoy networks designed to attract and study attackers’ behavior. Collaboration plays an equally important role, as organizations frequently share intelligence with partners, industry peers, and cybersecurity communities to create a more resilient collective defense. In addition, technical analysis, such as examining malware samples, investigating intrusion attempts, and analyzing network traffic, provides deeper insight into attack patterns and helps identify vulnerabilities that may be exploited.
7.4 Legal and Ethical Challenges in CYBINT
Despite its strategic importance, CYBINT presents significant legal and ethical challenges. Privacy concerns arise when monitoring online activities intersects with individual rights and civil liberties. Cyber threats frequently transcend national borders, creating jurisdictional complexities that demand international cooperation and compliance with diverse legal frameworks. More contentious still are offensive CYBINT practices, such as “hacking back,” which raise questions of legality, proportionality, and potential escalation of conflicts. Attribution also remains a major challenge, as accurately linking cyberattacks to specific actors is technically complex and fraught with political and diplomatic consequences.
In conclusion, Cyber Intelligence (CYBINT) has become indispensable in addressing cyber threats and vulnerabilities in the digital age. The discipline's focus on cyber threat intelligence (CTI) helps organizations stay ahead of potential attacks and bolster their cybersecurity defenses. Through various techniques such as passive and active collection, collaboration, and technical analysis, CYBINT enhances the understanding of cyber threats and aids in developing effective cybersecurity strategies. However, legal and ethical considerations must guide CYBINT activities to ensure the protection of privacy rights, respect international law, and promote responsible and accountable intelligence practices in the ever-evolving cyber landscape.
Imagery Intelligence (IMINT)
8.1 Introduction to IMINT and Its Evolution
Imagery Intelligence (IMINT) is an intelligence discipline concerned with the collection, analysis, and interpretation of visual imagery from different sources. It has a long history, beginning with aerial reconnaissance in the early 20th century, and has developed extensively alongside technological advancements. Today, IMINT plays a crucial role in providing insights into human activity, facilities, and terrain, serving both military and civilian applications.
8.2 IMINT Sensors and Platforms
IMINT relies on a variety of sensors and platforms to capture imagery. Satellites deliver high-resolution coverage of vast areas across the globe, offering perspectives that are critical for monitoring activities from space. Drones, or Unmanned Aerial Vehicles (UAVs), provide real-time and on-demand imagery for specific locations, allowing targeted intelligence gathering. Traditional manned aircraft, equipped with advanced imaging sensors, remain valuable for their flexibility and precision. In addition, ground-based sensors, both fixed and mobile, contribute to monitoring specific sites and situations, particularly when aerial or orbital platforms are not practical.
8.3 Interpretation and Analysis of IMINT Data
Once imagery is collected, analysts interpret and analyze it to extract meaningful intelligence. Using photogrammetry, they can calculate distances, elevations, and object dimensions, thereby producing detailed spatial data. Imagery analysts also work to identify infrastructure, facilities, and terrain features, while tracking changes over time to reveal patterns of activity. This analytical process is vital in creating situational awareness and supporting intelligence reporting.
8.4 Advancements in IMINT Technologies
Recent technological developments have significantly enhanced the power of IMINT. High-resolution satellite and sensor systems now produce imagery with remarkable clarity, enabling more precise assessments. Hyperspectral imaging adds another layer of depth by capturing data across multiple spectral bands, which allows analysts to detect materials, vegetation conditions, and other subtle features not visible to the naked eye. Synthetic Aperture Radar (SAR) has also revolutionized IMINT by penetrating cloud cover and operating in all weather conditions, an essential feature for both military operations and disaster response. Furthermore, advances in three-dimensional reconstruction now make it possible to build accurate 3D models from imagery, improving visualization and interpretation.
In conclusion, Imagery Intelligence (IMINT) is a vital intelligence discipline that harnesses visual imagery from various sensors and platforms. Its evolution from aerial reconnaissance to advanced satellite and drone technologies has significantly enhanced its capabilities. IMINT plays a pivotal role in providing critical insights into various areas of interest, supporting decision-making, military operations, disaster response, and other applications. With continued advancements in IMINT technologies, the discipline's potential for extracting valuable intelligence is expected to expand further, reinforcing its importance in the intelligence community.Read Also: The Role of Government Policies in Perpetuating the Eviction Crisis
Covert Intelligence Collection
9.1 Covert Operations and Intelligence Gathering
Covert intelligence collection refers to the secret acquisition of information without the knowledge of the target. This often involves undercover agents or the use of clandestine techniques to obtain sensitive or classified data. The primary objective is to protect the identity of both intelligence personnel and their sources, ensuring operations remain undetected. The element of secrecy is central, as it preserves the effectiveness of intelligence activities and prevents adversaries from taking countermeasures.
9.2 Importance of Covert Collection in National Security
The value of covert collection lies in its ability to access information from high-risk or hostile environments where overt methods would be impossible or dangerous. Through clandestine means, intelligence agencies are able to monitor adversaries, terrorist groups, and organized crime networks without alerting them. This intelligence not only supports strategic decision-making but also enhances national security by enabling preemptive measures, such as counterterrorism operations or diplomatic interventions. In this way, covert collection provides a decisive strategic advantage by delivering insights that cannot be obtained through open or technical means alone.
9.3 Ethical and Legal Implications of Covert Intelligence Collection
Despite its importance, covert intelligence collection raises complex ethical and legal concerns. Deception, manipulation, or intrusion into private domains are often integral to such operations, which can create significant moral dilemmas. Proportionality becomes a guiding principle: the potential benefits to national security must outweigh the risks and impacts on individual rights. Furthermore, accountability is critical. Covert activities must be subject to oversight to ensure compliance with both domestic and international laws, preventing abuses of power and safeguarding human rights. Upholding the rule of law is essential, as violations of sovereignty or extrajudicial actions can undermine the legitimacy of intelligence operations and damage international relations.
In conclusion, covert intelligence collection plays a significant role in national security, providing critical information from high-risk and sensitive environments. It allows intelligence agencies to operate discreetly and gather vital data without alerting potential adversaries. However, conducting covert operations raises ethical and legal concerns, necessitating careful consideration of the proportionality, accountability, and adherence to the rule of law. A balance between the necessity of covert intelligence gathering and ethical principles ensures responsible use of covert methods in safeguarding national interests and security.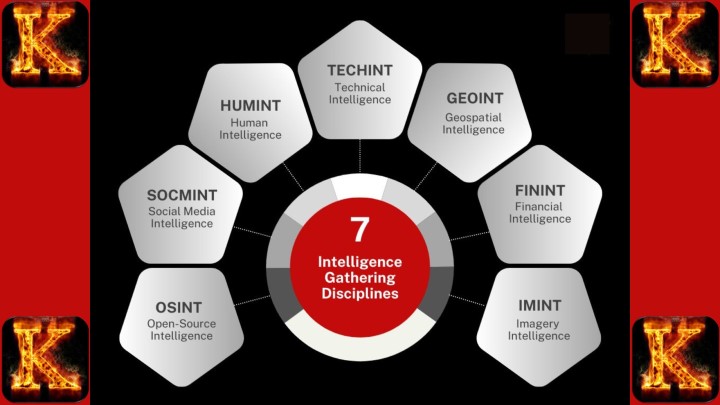
Technical Intelligence (TECHINT)
10.1 Understanding TECHINT and its Objectives
Technical Intelligence, commonly referred to as TECHINT, is a discipline within the intelligence community that focuses on collecting and analyzing technical data about foreign weapon systems, equipment, and technologies. Its central purpose is to provide insights into the capabilities, vulnerabilities, and advancements of adversaries’ military hardware and technological infrastructure. By doing so, TECHINT supports defense planning, guides acquisition decisions, and helps counter potential threats posed by foreign innovations.
10.2 Collection Techniques in TECHINT
The collection of technical intelligence employs a range of methods, each designed to uncover different aspects of foreign technologies. Analysts often examine and reverse-engineer captured enemy equipment or weapons to better understand their design, performance, and limitations. Signal intelligence (SIGINT) contributes by intercepting and studying electronic emissions and communications related to foreign technologies, while imagery intelligence (IMINT) offers satellite and aerial perspectives on military installations and equipment. In the digital era, cyber intelligence (CYBINT) has become increasingly vital, as it allows for the monitoring of cyber threats and the evaluation of foreign actors’ cyber capabilities.
10.3 Challenges and Limitations in TECHINT
Despite its importance, TECHINT faces several challenges. Accessing advanced foreign technologies and weapon systems is often restricted or requires high-risk operations. The growing complexity of modern technologies demands highly specialized expertise and advanced infrastructure for proper analysis. Adversaries may also employ deception and disinformation strategies to obscure their true capabilities, complicating accurate assessments. Furthermore, the rapid pace of technological advancement makes it difficult for intelligence agencies to remain current and adapt quickly to emerging threats.
10.4 Integration of TECHINT with Other Intelligence Disciplines
TECHINT rarely operates in isolation. Its value is enhanced when combined with other intelligence disciplines. Human intelligence (HUMINT) can provide contextual information on the intentions and decision-making processes behind technological development. SIGINT complements TECHINT by supplying data on the electronic signatures and communications associated with foreign systems, while IMINT provides visual confirmation and situational awareness. This integration ensures a more complete and accurate intelligence picture, strengthening analysis and supporting national security planning.
In conclusion, Technical Intelligence (TECHINT) serves as a crucial intelligence discipline for understanding foreign weapon systems, equipment, and technological advancements. By employing various collection techniques and integrating TECHINT with other intelligence disciplines, analysts can gain comprehensive insights into adversaries' capabilities and vulnerabilities. However, TECHINT faces challenges in accessing technology, dealing with technological complexities, and countering deception tactics. Overcoming these challenges and leveraging TECHINT's strengths contributes to informed decision-making and enhances national defense and security strategies.Read Also: How to Write a Handout for a Master’s Assignment
Measurement of Effectiveness in Intelligence Collection
Key Metrics of Effectiveness
Measuring the effectiveness of intelligence collection requires evaluating whether the information provided to decision-makers is accurate, timely, and useful. The most widely recognized metrics include:
-
Timeliness – Intelligence must reach decision-makers quickly enough to influence outcomes.
-
Accuracy – Information should reflect ground realities with minimal error.
-
Relevance – Data collected must align with the specific objectives or mission.
-
Completeness – Intelligence should provide a comprehensive picture without critical gaps.
-
Actionability – Information must support decision-making and lead to practical action.
Challenges in Assessment
Although these metrics provide a structured framework, evaluating effectiveness is not straightforward. Attribution is particularly difficult, as the direct contribution of specific intelligence efforts to broader outcomes is often unclear. Covert operations add another layer of complexity, since secrecy can prevent transparent evaluation. Information overload, caused by the sheer volume of data collected, also reduces clarity and usability. Moreover, some intelligence activities yield benefits only in the long term, making immediate assessment challenging.
Strategies for Improvement
Improving effectiveness depends on continuous learning and adaptation. Regular evaluation of collection strategies ensures responsiveness to changing conditions. Analyst feedback is crucial, as those interpreting the data can best identify strengths and weaknesses. Collaboration across agencies enhances overall effectiveness by pooling expertise and avoiding duplication. Technological innovation offers new tools for data collection and analysis, while red teaming, simulated adversarial exercises, provides an effective way to test systems and uncover blind spots.
In conclusion, measuring the effectiveness of intelligence collection is crucial to ensure that decision-makers receive accurate, timely, and actionable information. Metrics such as timeliness, accuracy, relevance, completeness, and actionability help gauge intelligence success. However, challenges in attribution, covert operations, information overload, and assessing long-term impact necessitate continuous improvement efforts. By incorporating feedback, promoting collaboration, embracing technological advancements, and engaging in red teaming exercises, intelligence agencies can enhance their collection methods and provide more valuable insights for effective decision-making and national security.Read Also: Police Community Relations: Building Trust and Collaboration
Future Trends in Intelligence Collection
12.1 Technological Advancements and Their Impact on Intelligence Gathering
Emerging technologies are reshaping the way intelligence is collected, processed, and applied. Advanced sensors, such as hyperspectral imaging and quantum-based systems, will provide more detailed and precise data, greatly expanding the scope of information available. Similarly, space-based intelligence will evolve as smaller and more affordable satellites, often deployed in constellations, make it possible to achieve continuous global coverage and real-time monitoring.
The explosion of data from diverse sources is also pushing agencies toward big data analytics and machine learning, which can sift through vast quantities of information to uncover patterns and insights that human analysts might otherwise miss. The Internet of Things (IoT) adds another dimension, as billions of interconnected devices generate streams of potentially valuable intelligence data, while simultaneously introducing new cybersecurity risks. Finally, blockchain technology is expected to influence intelligence practices by enhancing the security and transparency of data transactions and communications.
12.2 The Role of Artificial Intelligence in Intelligence Collection
Artificial Intelligence (AI) will play a central role in the future of intelligence gathering. Automated tools, such as AI-powered bots and web crawlers, can streamline open-source intelligence (OSINT) by continuously harvesting online information. Beyond collection, AI-driven predictive analysis enables agencies to anticipate threats by identifying hidden patterns and long-term trends across multiple datasets.
Natural Language Processing (NLP) further enhances intelligence by allowing machines to analyze unstructured text, such as social media posts or online news, to assess sentiment and public opinion. Additionally, image and speech recognition technologies powered by AI expand the capacity to analyze multimedia data, strengthening imagery intelligence (IMINT) and voice-based monitoring systems. Together, these innovations are expected to transform not only the scale but also the precision of intelligence operations.
12.3 Ethics and Governance in the Era of Advanced Intelligence Methods
The increasing sophistication of intelligence collection raises profound ethical and governance challenges. As surveillance capabilities expand, so too do concerns regarding privacy, civil liberties, and data protection. AI introduces further risks by inheriting biases from training datasets, which can compromise fairness and accuracy in intelligence assessments.
Ensuring accountability and transparency will therefore require stronger governance frameworks, including oversight mechanisms to regulate the use of advanced technologies. Moreover, many of these technologies are dual-use, meaning they can serve both defensive and malicious purposes. This duality underscores the need for responsible innovation, clear legal boundaries, and international agreements on export controls to prevent misuse.
In conclusion, the future of intelligence collection will be heavily influenced by technological advancements, particularly in sensors, data analytics, AI, and space-based intelligence. These innovations will provide new opportunities for gathering valuable insights while also presenting ethical and governance challenges. As intelligence agencies adopt these advanced methods, ensuring privacy, fairness, accountability, and adherence to ethical principles will be paramount. Responsible and transparent use of these technologies is essential to build public trust, protect individual rights, and promote the legitimate and effective use of intelligence collection in addressing national security challenges.
Comments are closed!