Client-server architecture is a fundamental concept in computer networking that revolutionizes how devices communicate and share resources. In computer networking, the client-server architecture is a cornerstone, facilitating efficient communication, resource sharing, and data management across networks. This comprehensive guide will delve into the intricacies of client-server architecture in computer networking, exploring its advantages, examples, and applications. By understanding this architecture, businesses and individuals can optimize their network infrastructure for enhanced performance, security, and scalability.
Client-server architecture in computer networking refers to a distributed computing model where tasks and resources are divided between client devices and server systems. Clients initiate requests for services or resources, while servers fulfill these requests by providing the requested services or resources. This architecture is characterized by its hierarchical structure, with servers acting as centralized repositories of data and services and clients accessing and utilizing these resources as needed.


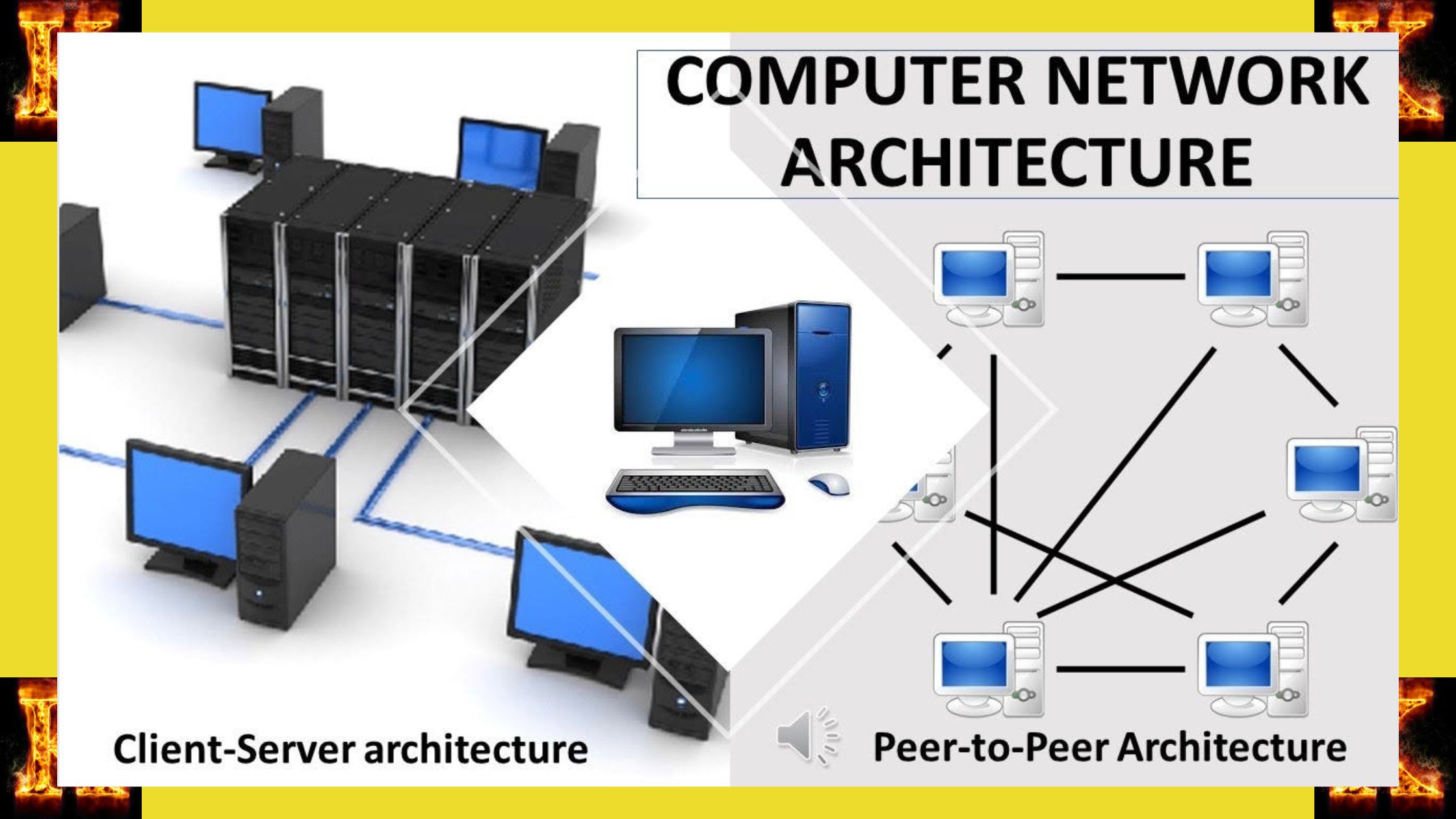
Types of Network Architecture
In network architecture, understanding the various types is crucial for designing and implementing efficient communication systems. Three primary types of network architecture include client-server architecture, peer-to-peer (P2P) architecture, and hybrid architecture. Each type offers unique features and functionalities tailored to specific networking requirements.
Client-Server Architecture:
- Client-server architecture follows a centralized model where servers manage and distribute client resources.
-
Characteristics:
- Servers act as centralized repositories of data and services, fulfilling client requests.
- Clients initiate requests for services or resources from servers.
-
Advantages:
- Scalability: Allows seamless addition of clients and servers without compromising performance.
- Centralized Management: Simplifies administration tasks by centralizing resource and data management.
- Security: Enables robust security measures through centralized control and authentication mechanisms.
-
Disadvantages:
- Single Point of Failure: The reliance on centralized servers creates a single point of failure, making the network vulnerable to disruptions.
- Complexity: Setting up and maintaining client-server architectures can be complex and resource-intensive, requiring skilled personnel and specialized hardware.
- Cost: Initial setup and ongoing maintenance expenses associated with servers and network infrastructure can be substantial, especially for small-scale deployments.
Peer-to-Peer (P2P) Architecture:
- P2P architecture decentralizes resource management, allowing peers to interact directly.
-
Characteristics:
- Peers serve as clients and servers, sharing resources and data.
- No centralized server is required, promoting decentralized resource distribution.
-
Advantages:
- Decentralization: Eliminates single points of failure and promotes fault tolerance.
- Resource Sharing: Facilitates direct resource sharing among peers without relying on centralized servers.
-
Disadvantages:
- Limited Scalability: May face scalability challenges due to the absence of centralized resource management.
- Security Concerns: Peer-to-peer networks can be vulnerable to security threats and unauthorized access.

Hybrid Architecture:
- Hybrid architecture combines elements of both client-server and P2P architectures, offering a flexible and adaptable approach to network design.
-
Characteristics:
- Integrates centralized and decentralized components to optimize resource management and distribution.
- Allows for the coexistence of client-server and peer-to-peer functionalities within the same network.
-
Advantages:
- Flexibility: Provides flexibility in leveraging the benefits of client-server and P2P architectures.
- Scalability: Offers scalability benefits by combining centralized and decentralized resource management.
-
Disadvantages:
- Complexity: Hybrid architectures may introduce additional network design and management complexity.
- Maintenance: Requires careful planning and maintenance to ensure seamless integration of centralized and decentralized components.
Read Also: My Reflection about Computer Assembly
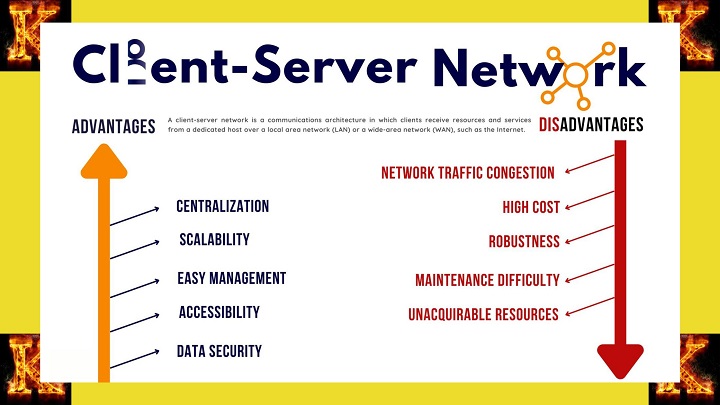
Advantages of Client-Server Architecture
Client-server architecture in computer networking, also known as the client-server model, is a distributed computing paradigm in which computers in a network are divided into clients and servers. Clients initiate requests for services or resources, while servers fulfill these requests by providing the requested services or resources. This architecture offers several advantages over other computing approaches, including:- Scalability: Unlike Peer-to-Peer (P2P) and monolithic computing approaches, client-server architecture allows for easy scalability. Additional clients and servers can be added to the network without compromising performance, making it ideal for growing organizations.
- Centralized Management: Client-server architecture facilitates centralized management of data and resources, simplifying administration tasks. This centralized approach enhances efficiency and security compared to decentralized architectures.
- Security: The centralized nature of client-server architecture enables robust security measures such as authentication, encryption, and controlled access. This ensures data integrity and confidentiality, mitigating security risks.
- Efficiency: By distributing computational tasks between clients and servers, client-server architecture reduces the workload on individual machines, leading to improved efficiency and performance. This efficiency surpasses that of monolithic, P2P, and mainframe architectures.
- Reliability: Client-server architecture incorporates failover and redundancy mechanisms, enhancing reliability and fault tolerance. In server failures, failover mechanisms ensure uninterrupted service delivery, minimizing downtime.
- Collaboration: With shared access to data and resources, client-server architecture fosters user collaboration. This collaborative environment promotes productivity and innovation, making it advantageous for collaborative projects and team-based work.

Examples of Client-Server Networks
One classic example of a client-server network is the World Wide Web (WWW), where web browsers (clients) communicate with web servers to retrieve and display web pages. In this scenario, clients send requests for specific web content, such as web pages or multimedia files, to web servers, which respond by delivering the requested content to the clients.Critical Components of the Client-Server Network:
- Web Browsers (Clients): Web browsers, such as Google Chrome, Mozilla Firefox, and Microsoft Edge, act as client applications that enable users to access and navigate the World Wide Web. Users initiate requests for web content by entering URLs or clicking on links within the browser interface.
- Web Servers: Web servers, such as Apache HTTP Server, Nginx, and Microsoft Internet Information Services (IIS), host and serve web content to clients upon receiving requests. These servers store HTML files, multimedia resources, scripts, and other web assets, delivering them to clients in response to their requests.
Workflow of Client-Server Communication in the WWW:
- Client Request: A user launches a web browser and enters a URL (Uniform Resource Locator) or clicks on a hyperlink to access a specific web page or resource.
- HTTP Request: The web browser sends an HTTP (Hypertext Transfer Protocol) request to the appropriate web server identified by the URL provided. The request contains information such as the requested resource and any additional parameters.
- Server Processing: Upon receiving the request, the web server processes the HTTP request, retrieves the requested web page or resource from its storage, and prepares a response to send back to the client.
- HTTP Response: The web server constructs an HTTP response containing the requested web content and metadata, such as headers and status codes. The response is then transmitted back to the client over the network.
- Client Rendering: Upon receiving the HTTP response, the web browser renders the web content from the server, displaying it to the user within the browser window. Users can interact with the displayed content, such as clicking links or submitting forms.
- Content Display: The web browser renders the HTML, CSS, JavaScript, images, and other resources included in the web page, presenting the final rendered page to the user for viewing and interaction.
Advantages of Client-Server Networks in WWW:
- Scalability: Client-server architecture allows for scalable deployment of web applications, enabling servers to handle multiple client requests simultaneously without significant performance degradation.
- Centralized Management: Web servers facilitate centralized management and distribution of web content, ensuring consistency, reliability, and security across the network.
- Resource Sharing: Clients can access a wide range of web resources hosted on remote servers, including web pages, documents, multimedia files, and web applications, enhancing collaboration and information sharing.
- Security: Web servers implement security measures such as encryption, authentication, and access control to protect sensitive data and prevent unauthorized access or tampering.

Client-server architecture in Database Management Systems (DBMS)
Client-server architecture in database management systems (DBMS) is a fundamental framework to effectively streamline data management and retrieval processes. Within this architecture, client applications, serving as end-user interfaces, communicate with dedicated database servers to execute various operations such as data querying, updating, and deletion. This architecture separates data processing responsibilities between clients and servers, with clients initiating requests for specific data operations and servers executing those requests by accessing and managing the underlying database.Critical Components of Client-Server Architecture in DBMS:
- Client Applications are software programs or interfaces end-users utilize to interact with the database system. Clients send requests to the server to perform operations on the database, such as retrieving records or updating data.
- Database Servers: Database servers are responsible for storing, managing, and processing the data stored within the database system. They respond to client requests by executing SQL queries, retrieving or modifying data, and returning results to the client applications.
Advantages of Client-Server Architecture in DBMS:
- Centralized Data Management: Client-server architecture ensures data consistency and integrity across the entire system by centralizing data storage and management on dedicated database servers.
- Scalability: Client-server architecture allows easy scalability by adding more client machines or upgrading server hardware to accommodate growing data and user demands.
- Enhanced Security: Database servers can implement robust security measures such as authentication, access control, and encryption to safeguard sensitive data stored within the system.
- Concurrency Control: Client-server DBMS systems often incorporate mechanisms for managing concurrent access to data, ensuring consistency, and preventing data corruption in multi-user environments.
Example of Client-Server DBMS:
- MySQL: MySQL is a popular open-source relational database management system that follows the client-server architecture model. Client applications like web or desktop applications connect to MySQL database servers to perform various data operations.
- Microsoft SQL Server: Microsoft SQL Server is a comprehensive relational DBMS developed by Microsoft and widely used in enterprise environments. It employs a client-server architecture to facilitate efficient data management and transaction processing.
- Oracle Database: Oracle Database is a robust and scalable relational database management system known for its reliability and performance. It utilizes client-server architecture to support diverse applications and workloads.
Read Also: TechFite Case Study
Common Types of Computer Networks
Computer networks are diverse, comprising several types designed to meet specific needs and operating environments. Some common types of computer networks include:- Local Area Networks (LANs): LANs connect devices within a limited geographical area, such as an office building, school campus, or home. They facilitate fast data transfer and resource sharing among connected devices, typically using Ethernet cables or Wi-Fi.
- Wide Area Networks (WANs) span large geographical areas, connecting multiple LANs or individual devices over long distances. They rely on telecommunications infrastructure, such as leased lines, fiber-optic cables, or satellite links, to transmit data between distant locations.
- Metropolitan Area Networks (MANs): MANs cover larger areas than LANs but smaller areas than WANs, typically serving a city or metropolitan region. They offer high-speed connectivity and data exchange between various organizations, institutions, or government agencies within a city's boundaries.
- Wireless Networks: Wireless networks utilize radio waves or infrared signals to establish connections between devices without needing physical cables. They include Wi-Fi networks for local wireless connectivity and cellular networks for mobile communication over vast areas.
- Personal Area Networks (PANs): PANs connect personal devices, such as smartphones, tablets, laptops, and wearable gadgets, within the immediate vicinity of an individual. Bluetooth and Zigbee are standard technologies used to establish PANs for device-to-device communication.

Types of Wi-Fi
Wi-Fi, a ubiquitous wireless networking technology, encompasses several standards and iterations, each offering distinct features and capabilities. Some common types of Wi-Fi include:- Wi-Fi 4 (802.11n): Introduced in 2009, Wi-Fi 4 offers data transfer speeds of up to 600 Mbps and operates in both the 2.4 and 5 GHz frequency bands. It introduced multiple-input multiple-output (MIMO) technology for improved throughput and range compared to earlier standards.
- Wi-Fi 5 (802.11ac): Released in 2013, Wi-Fi 5 delivers significantly faster speeds than Wi-Fi 4, with theoretical maximum speeds reaching up to 3.5 Gbps. It operates exclusively in the 5 GHz frequency band and introduces features like beamforming and MU-MIMO (multi-user, multiple-input, multiple-output) for enhanced performance in crowded environments.
- Wi-Fi 6 (802.11ax): Introduced in 2019, Wi-Fi 6 represents a significant advancement in wireless technology, offering higher throughput, lower latency, and improved efficiency compared to previous standards. It supports multi-user connectivity and operates in 2.4 and 5 GHz bands, with theoretical speeds exceeding 9.6 Gbps.
- Wi-Fi 6E: Wi-Fi 6E is an extension of Wi-Fi 6 that utilizes the 6 GHz frequency band in addition to the existing 2.4 GHz and 5 GHz bands. By leveraging additional spectrum, Wi-Fi 6E offers increased capacity and reduced interference, enabling higher performance and reliability for Wi-Fi networks.
Read Also: Assembling a CPU: A Comprehensive Guide
Different Types of Topologies
Network topology, the arrangement of devices and connections in a network, is crucial in determining its efficiency and reliability. Here are some common types of network topologies:-
Star Topology:
- In a star topology, all devices are connected to a central hub or switch, forming a star-like structure.
- Advantages: Easy to install, centralization simplifies management, and failures in one device do not affect others.
- Limitations: Dependency on the central hub, potential single point of failure if the hub malfunctions.
-
Bus Topology:
- In a bus topology, all devices are connected to a cable called the bus, with terminators at each end.
- Advantages: Simple and inexpensive to set up, suitable for small networks with few devices.
- Limitations: Susceptible to cable failures, challenging to scale, and performance degrades as more devices are added.
-
Ring Topology:
- In a ring topology, devices are connected in a closed loop, where each device is connected to exactly two other devices.
- Advantages: Efficient use of network bandwidth, no collisions in data transmission.
- Limitations: Difficulty in reconfiguring or expanding; failure of one device can disrupt the entire network.
-
Mesh Topology:
- In a mesh topology, every device is connected to another device, creating a redundant network.
- Advantages: High fault tolerance, data can take multiple paths, and no single point of failure exists.
- Limitations: Expensive to implement and maintain, complex wiring and configuration.
-
Hybrid Topology:
- A hybrid topology combines two or more topologies, such as star-bus or star-ring.
- Advantages: Offers flexibility and scalability and can tailor the network to specific requirements.
- Limitations: Complexity increases when combining topologies, requiring careful planning and management.

Comments are closed!